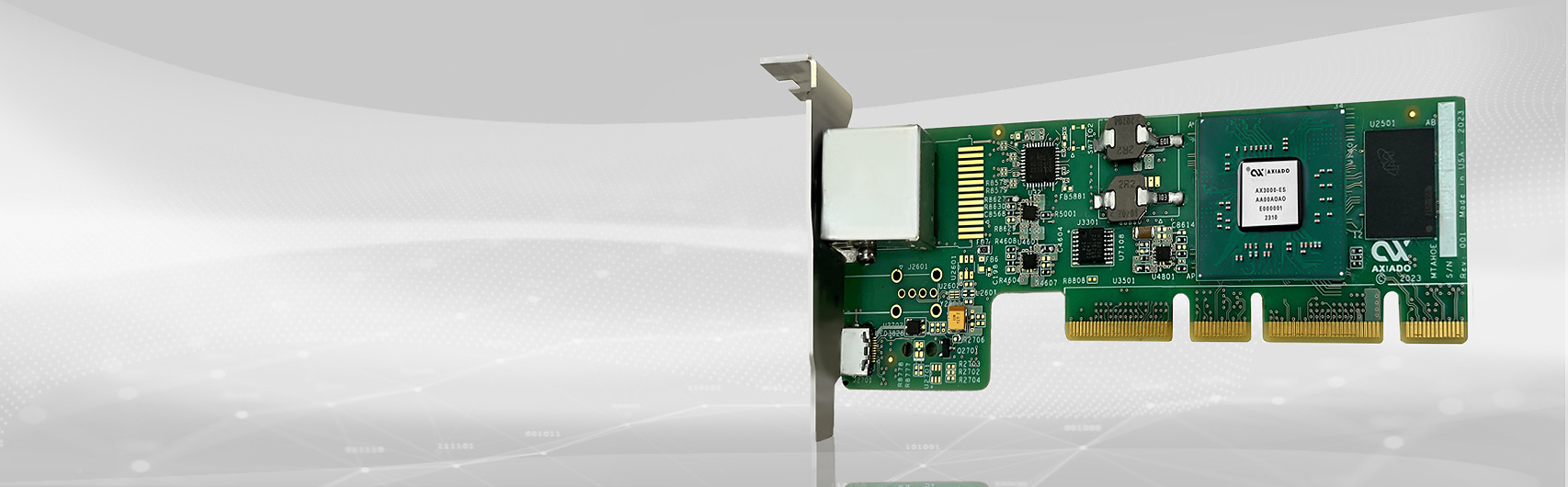
Axiado’s Leading Portfolio of SoC & Modules
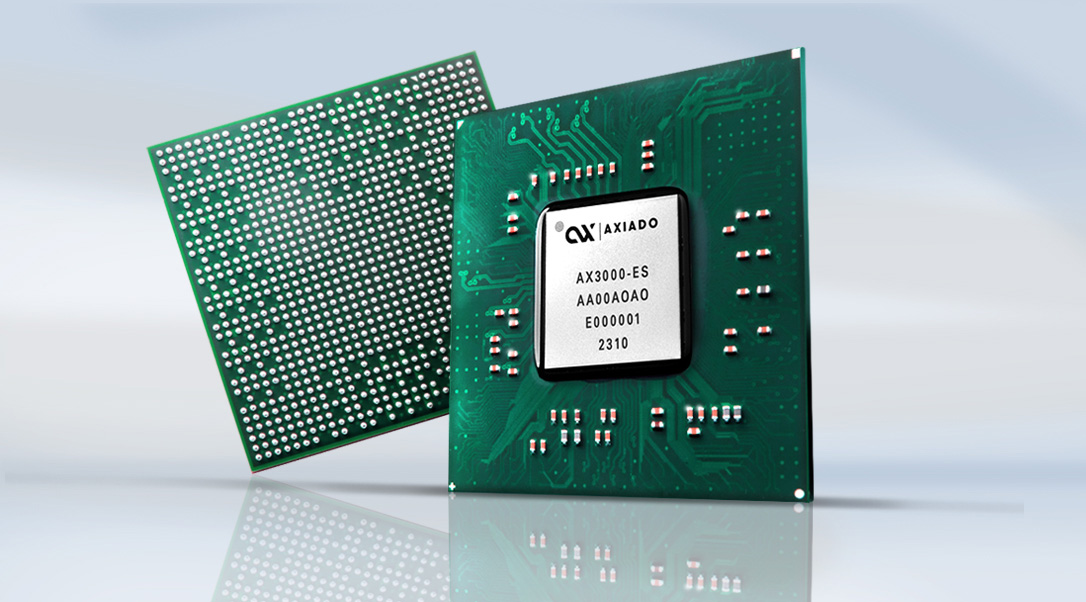
AX3000/AX2000 TCU
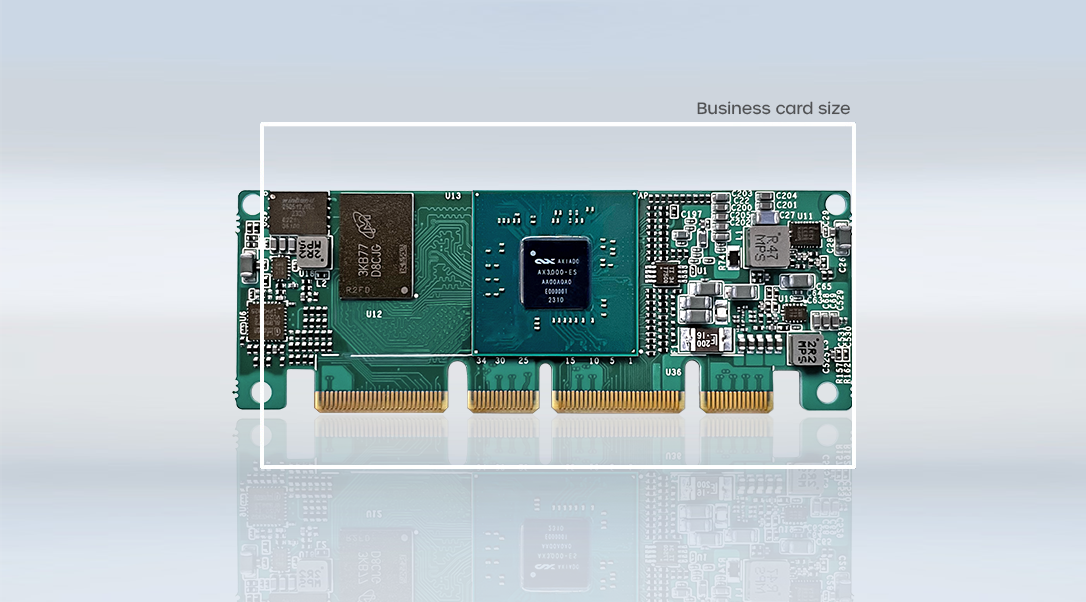
The Axiado AX3000/AX2000 SoC with built-in AI provides the industry’s most robust, hardware-anchored solution to detect and defend against ransomware and cyberattacks in cloud datacenters, 5G networks, and network switches. Compact yet powerful, this 23×23 BGA SoC draws under 5W while featuring anti-tamper and anti-counterfeit hardware, virtualization capabilities, and safeguards against sophisticated attacks.
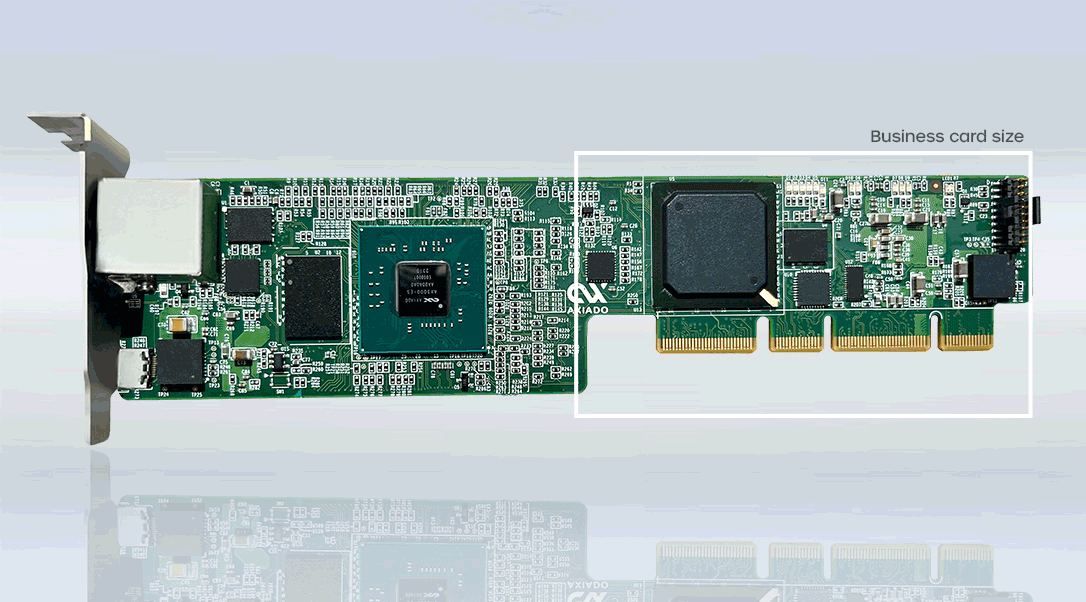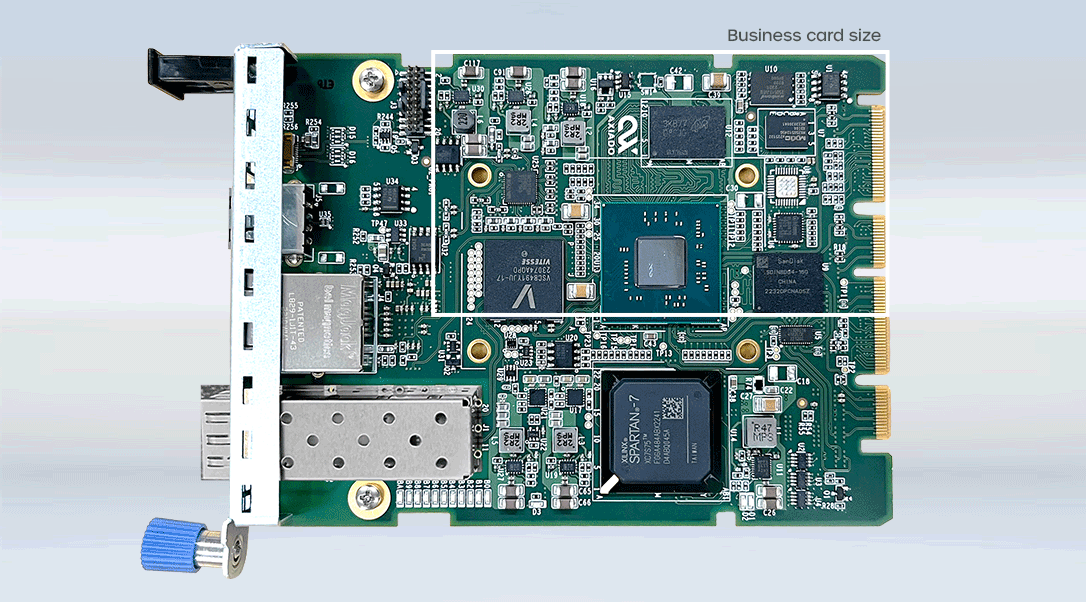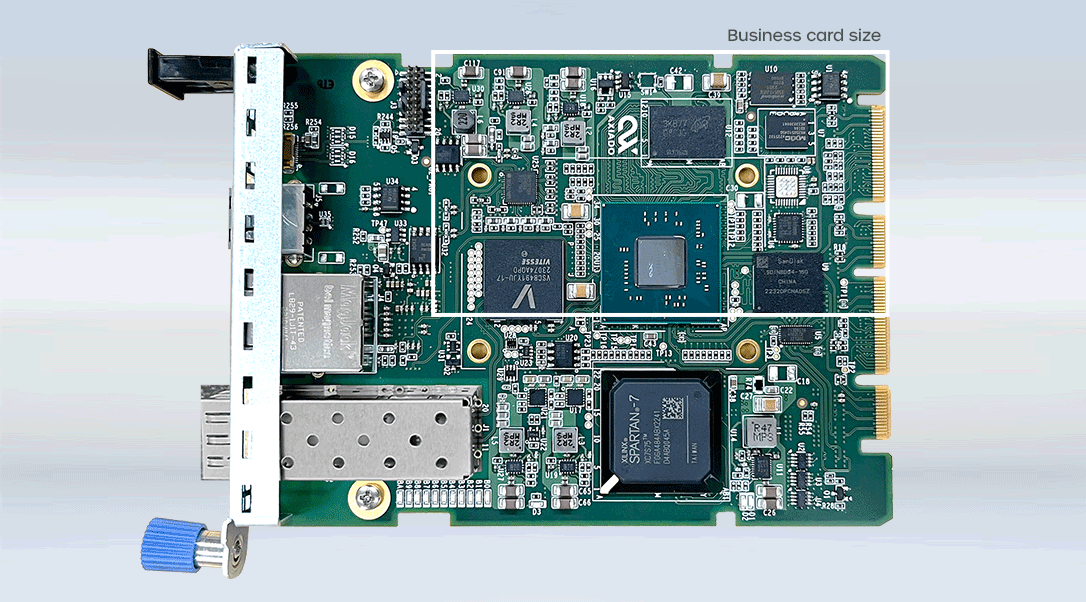
Smart-SCM
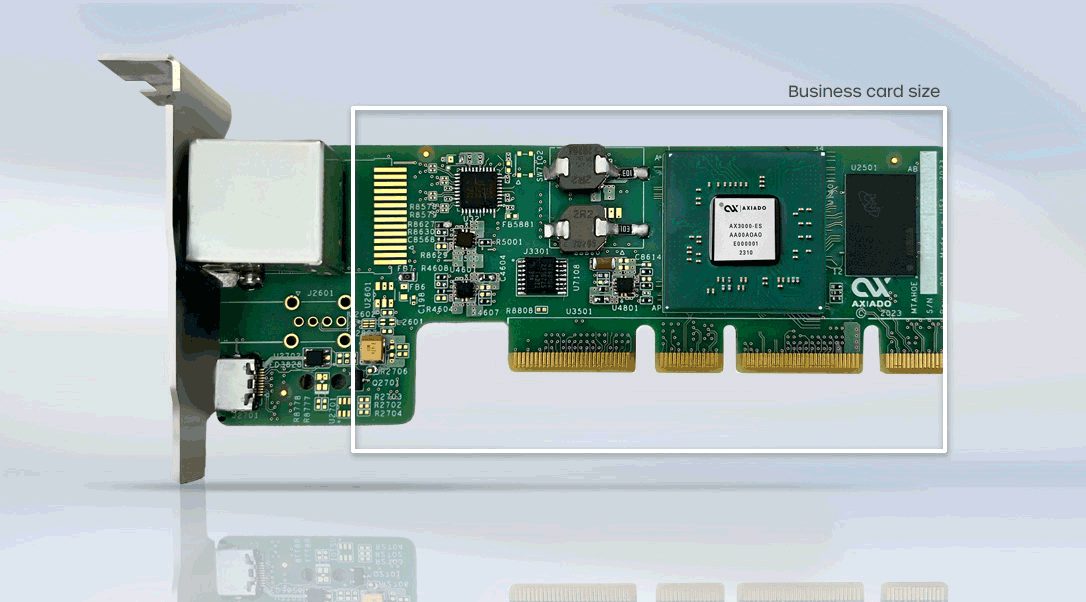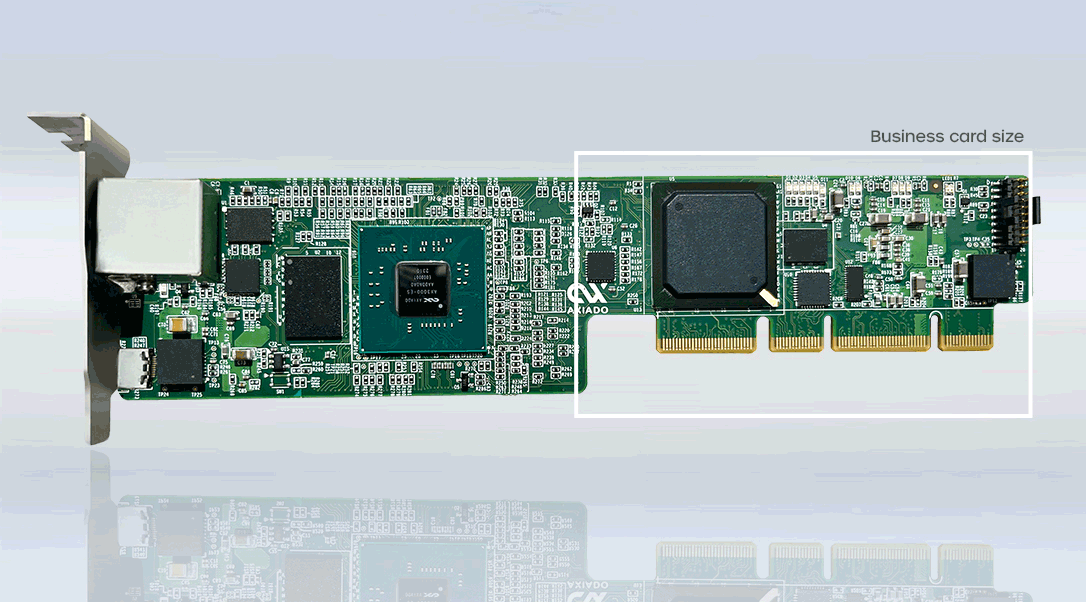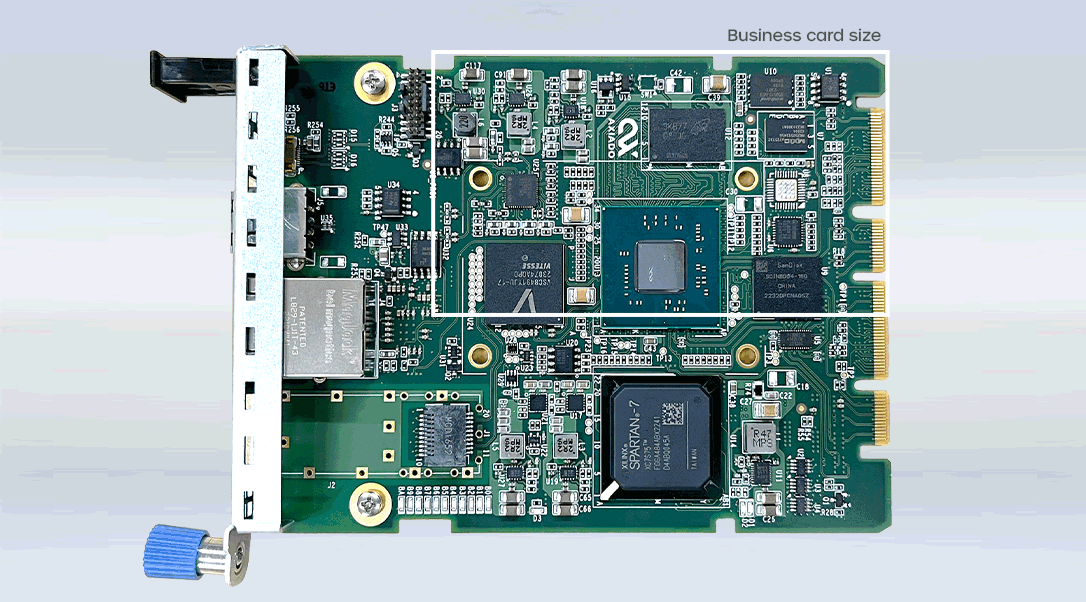
The Axiado Smart Secure Control Module (Smart-SCM) powered by the TCU (in, for example, 1U vertical form factor) complies with the OCP DC-SCM standard, making it ideal for datacenters. Our TCUs combine silicon, AI and data collection, and software into a compact, power-efficient TCU with unique AI functionality explicitly designed for security, safeguarding cloud datacenters and 5G networks (CU).
Secure-NCM
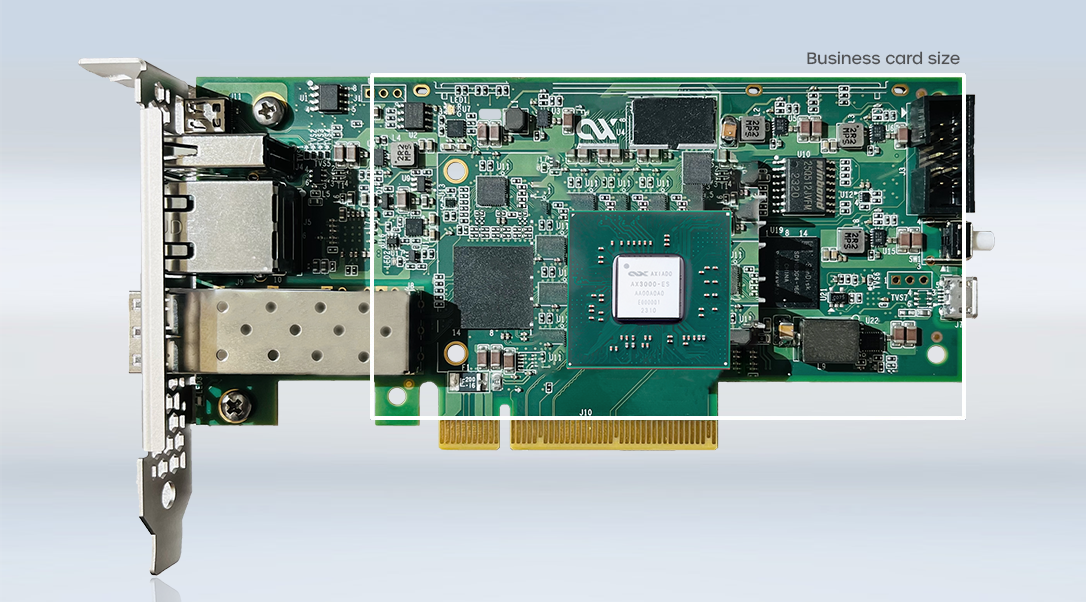
The Axiado compact Secure Network Compute Module (NCM) powered by the TCU provides smart network interfaces and security for network switches, 5G networks (DU) across campus, datacenter and service providers. TCU offers unique control/management plane SmartNIC capabilities for boot- and run-time operations. Service providers, enterprises and datacenter operators rely on TCU for secure remote provisioning, de-commissioning of platforms, and secure ownership transfers.
AI-Driven Secure Management Card
The Axiado AI-Driven Secure Management Card powered by the TCU (1U internal form factor) allows interoperability and provides enhanced security to next-generation servers, making it the best-in-class security solution for NVIDIA MGX platforms. In addition to being compact and power-efficient, the card features integrated ASIC with trusted computing, BMC, TPM, HRoT, NC-SI, and AI/ML all in a single device.
Axiado’s Leading Portfolio of SoC & Modules
Axiado AX3000/AX2000 TCU
The Axiado AX3000/AX2000 SoC with built-in AI provides the industry’s most robust, hardware-anchored solution to detect and defend against ransomware and cyberattacks in cloud datacenters, 5G networks, and network switches. Compact yet powerful, this 23×23 BGA SoC draws under 5W while featuring anti-tamper and anti-counterfeit hardware, virtualization capabilities, and safeguards against sophisticated attacks.
Axiado Smart-SCM Powered by TCU
The Axiado Smart Secure Control Module (Smart-SCM) powered by the TCU (in, for example, 1U vertical form factor) complies with the OCP DC-SCM standard, making it ideal for datacenters. Our TCUs combine silicon, AI and data collection, and software into a compact, power-efficient TCU with unique AI functionality explicitly designed for security, safeguarding cloud datacenters and 5G networks (CU).
Axiado Secure-NCM Powered by TCU
The Axiado compact Secure Network Compute Module (NCM) powered by the TCU provides smart network interfaces and security for network switches, 5G networks (DU) across campus, datacenter and service providers. TCU offers unique control/management plane SmartNIC capabilities for boot- and run-time operations. Service providers, enterprises and datacenter operators rely on TCU for secure remote provisioning, de-commissioning of platforms, and secure ownership transfers.
Axiado AI-Driven Secure Management Card Powered by TCU
The Axiado AI-Driven Secure Management Card powered by the TCU (1U internal form factor) allows interoperability and provides enhanced security to next-generation servers, making it the best-in-class security solution for NVIDIA MGX platforms. In addition to being compact and power-efficient, the card features integrated ASIC with trusted computing, BMC, TPM, HRoT, NC-SI, and AI/ML all in a single device.
Axiado’s single-chip TCU control plane is a hardware-anchored solution rooted in real-time and preemptive AI with preemptive threat detection. It provides comprehensive protection through a dedicated coprocessor to enable manufacturers to build solutions that are safe, secure, and resilient by design and default.
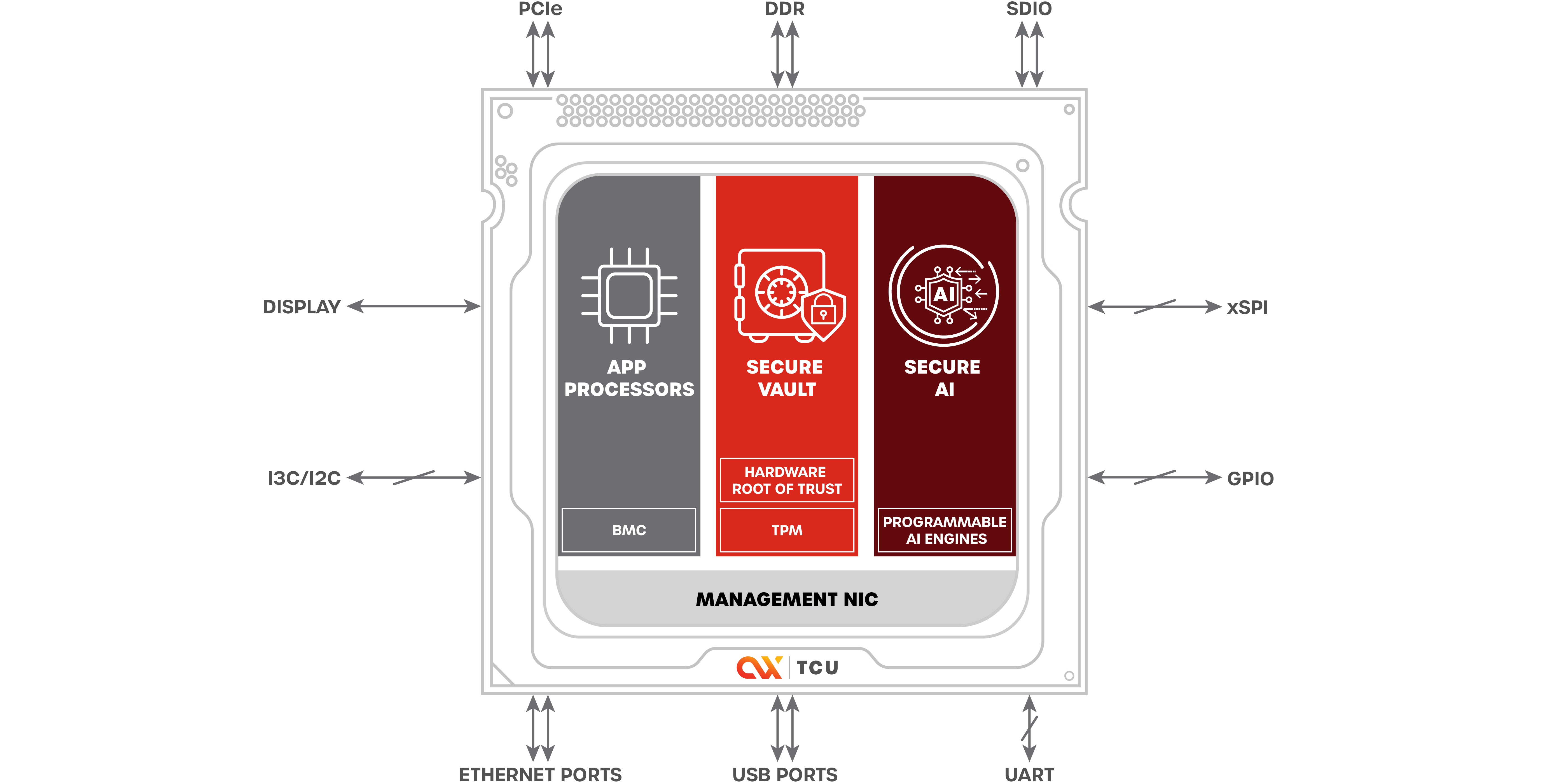
Axiado’s single-chip TCU control plane is a hardware-anchored solution rooted in real-time and preemptive AI with preemptive threat detection. It provides comprehensive protection through a dedicated coprocessor to enable manufacturers to build solutions that are safe, secure, and resilient by design and default.

To overcome the limitations of existing hardware security, Axiado reimagined Open Compute Project’s (OCP) trusted platform datacenter-ready secure control module (DC-SCM) and created the Smart-SCM card, powered by the Axiado TCU.
The differentiators make the Smart-SCM a novel, innovative and disruptive approach to security:
- World’s first RoT, BMC, TPM, HSM and firewall functions integrated into a single device
- Dedicated AI hardware for cybersecurity, providing preemptive protection against network- and peripheral-based, and physical side-channel attacks
- Enablement of virtual platforms with independent RoT, BMC, and trust agents on a single TCU
To overcome the limitations of existing hardware security, Axiado reimagined Open Compute Project’s (OCP) trusted platform datacenter-ready secure control module (DC-SCM) and created the Smart-SCM card, powered by the Axiado TCU.
The differentiators make the Smart-SCM a novel, innovative and disruptive approach to security:
- World’s first RoT, BMC, TPM, HSM and firewall functions integrated into a single device
- Dedicated AI hardware for cybersecurity, providing preemptive protection against network- and peripheral-based, and physical side-channel attacks
- Enablement of virtual platforms with independent RoT, BMC, and trust agents on a single TCU
Network infrastructure products like switches, service provider routers, 5G base stations require rethink from a security standpoint for inline data traffic. This includes protecting firmware, side-channel attack protection, DoS, privilege escalation, and detecting vulnerabilities at boot- and run-time. Axiado Secure-NCM based on TCU architecture offers a single-chip integration of platform security, network security and various anomaly detection capabilities. In summary, TCU-based solutions, in-real-time, help protect platform assets and detect vulnerabilities/attacks.
The key TCU-based solution differentiators are:
- Real-time AI-driven network and behavior anomaly detection
- Smart NIC capabilities of static, wildcard and denial-of-service rules enforcement
- Platform firmware protection, upgrades with resilience
Network infrastructure products like switches, service provider routers, 5G base stations require reboot from a security standpoint. This includes protecting firmware, side-channel attack protection, DoS, privilege escalation, and detecting vulnerabilities at boot- and run-time. Axiado NCM based on TCU architecture offers a single-chip integration of platform security, network security and various anomaly detection capabilities. In summary, TCU-based solutions, in-real-time, help protect platform assets and detect vulnerabilities/attacks.
The key TCU-based solution differentiators are:
- Real-time network and behavior anomaly detection
- Smart NIC capabilities of static, wildcard and denial-of-service rules enforcement
- Platform firmware protection, upgrades with resilience
As the industry’s best in-class security solution to protect AI/ML infrastructure, Axiado’s AI-Driven Secure Management Card is an internal form factor card that is designed specifically for all NVIDIA MGX platforms.
Key differentiators enabling AI-Driven Secure Management Card interoperability with NVIDIA MGX platforms:
- Integrated ASIC with trusted computing, BMC, TPM, HRoT, NC-SI and AI/ML in a single device
- Provides protection against insider and side-channel attacks through hardware agent-based behavioral ransomware detection
- Flexible platform ownership management, secure host connectivity and encrypted memory for data and code protection
As the industry’s best in-class security solution to protect AI/ML infrastructure, Axiado’s AI-Driven Secure Management Card is an internal form factor card that is designed specifically for all NVIDIA MGX platforms.
Key differentiators enabling AI-Driven Secure Management Card interoperability with NVIDIA MGX platforms:
- Integrated ASIC with trusted computing, BMC, TPM, HRoT, NC-SI and AI/ML in a single device
- Provides protection against insider and side-channel attacks through hardware agent-based behavioral ransomware detection
-
Flexible platform ownership management, secure host connectivity and encrypted memory for data and code protection
Leading The Industry Forward
Axiado’s TCU meets these urgently needed gaps in the cybersecurity industry
• Standards-based Interfaces and software packages
• Policy-based recovery to prior known state
• Decentralized key storage
• Application isolation in hardware
• Platform Root-of-Trust
• Integrity and confidentiality of control and management
• Proactive reports on state of platform
• Minimally invasive software updates
Leading The Industry Forward
Axiado’s TCU meets these urgently needed gaps in the cybersecurity industry:
• Standards-based Interfaces and software packages
• Policy-based recovery to prior known state
• Decentralized key storage
• Application isolation in hardware
• Platform Root-of-Trust
• Integrity and confidentiality of control and management
• Proactive reports on state of platform
• Minimally invasive software updates